Phishing Examples
Cybercriminals can target anyone, even you! If you see something suspicious report it.
Report Phishing Report Malware Report Issue or Incident
Phishing attacks often masquerade as trustworthy entities in an attempt to steal your personal, financial, or academic information. University members, including students, faculty, and staff, should remain vigilant. Below is a checklist and examples of common red flags to watch for in phishing messages:
[1697553827].jpg)
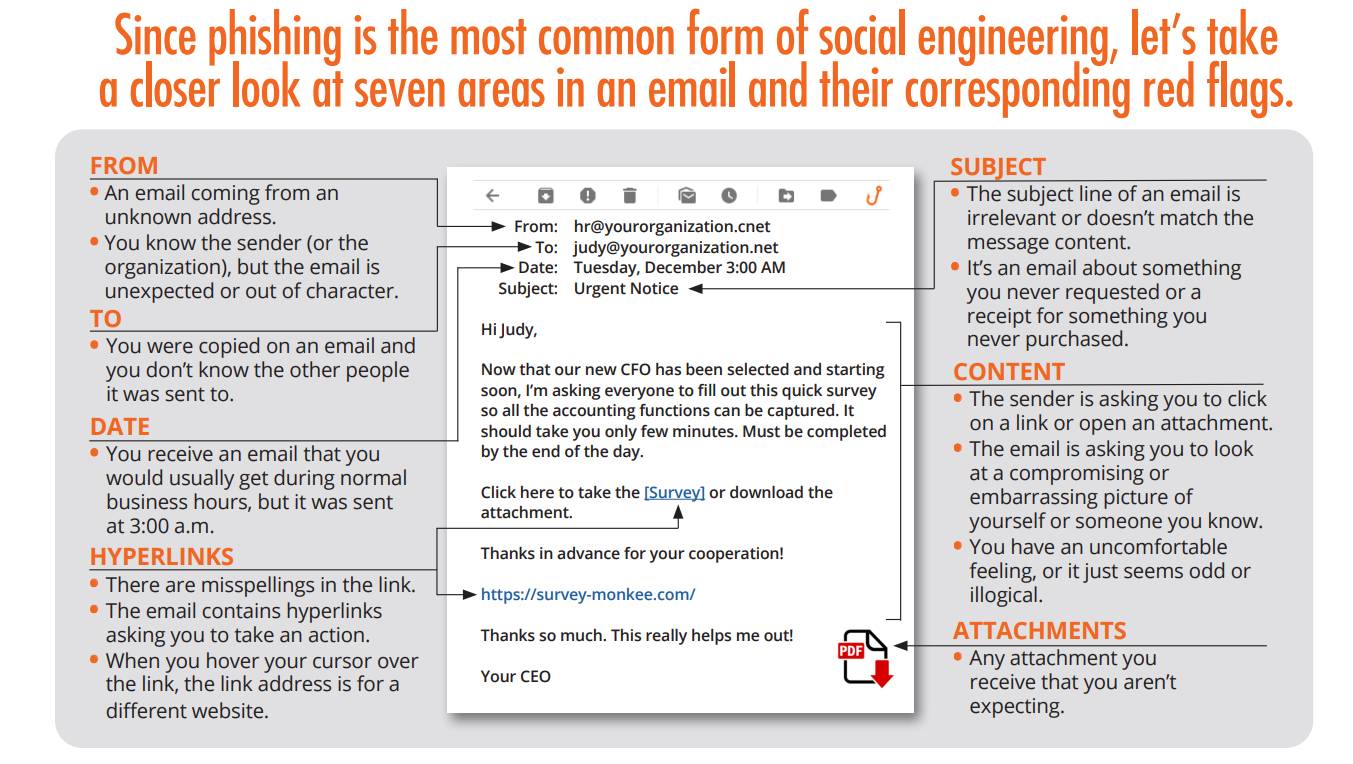
Phishing Red Flags
-
Suspicious Sender's Address:
- Emails that don’t come from official university domains (e.g., @universityname.edu).
- Look-alike domains with slight misspellings or additional characters.
-
Generic Salutations:
- Messages that use generic greetings such as "Dear User" or "Dear Account Holder" instead of your name.
-
Urgent or Threatening Language:
- Warnings about account closures, unauthorized activity, or messages that induce panic.
- Pressure to act quickly, often within a "short timeframe."
-
Unexpected Attachments or Links:
- Unsolicited attachments or links which you weren't expecting from the sender.
- Shortened or obfuscated URLs.
-
Requests for Personal or Financial Information:
- Any request for passwords, credit card details, social security numbers, or other sensitive information.
-
Grammatical and Spelling Errors:
- Poor grammar, awkward phrasing, or spelling mistakes.
- Inconsistencies in formatting or design compared to official university communications.
-
Mismatched URL:
- Hover over any links (without clicking) to see if the URL matches the link's anchor text or the email's purported sender.
-
Too Good to Be True:
- Offers of money, scholarships, or prizes that seem too generous or come out of nowhere.
-
Unexpected Transactional Emails:
- Notifications of purchases, transfers, or changes to your account that you didn’t initiate.
-
Non-standard Domain Names in Links:
- Instead of the usual ".edu," it might be something unrelated, like ".net" or ".info."
-
Pop-up Forms in Emails:
- Emails that prompt you to enter personal information directly into the email or a pop-up form.
-
Unfamiliar Senders:
- Messages from unfamiliar individuals or institutions that have no clear relation to you or the university.
-
Check the Signature:
- Lack of details about the signer or how you can contact the company or entity.
-
Unusual File Attachments:
- Unsolicited emails containing file types you wouldn't normally receive, especially .exe, .scr, .zip, or .rar files.
-
Lack of Transparency:
- The message makes it hard to verify its authenticity, like lacking contact details or referencing vague entities or events.
Protection Tips:
- Always verify the identity of anyone asking for personal or sensitive information.
- If in doubt, directly contact the university department or service in question using known contact information, not what's provided in the suspicious email.
- Utilize multi-factor authentication (MFA) when available.
- Regularly update and maintain antivirus and anti-malware software on all devices.
If you believe you've received a phishing email, do not respond, click on any links, or download any attachments. Report it to the university's IT department immediately. Stay safe and always be cautious!
If you believe you have encountered a phishing email, please forward it to [email protected] for review.
IT Security can help you determine whether the email is a scam and notify others.
